Secure VPN infrastructures at the Edge
Welotec VPN Security Suite
When managing a high number of distributed devices in the field, connectivity and device access is key. However, setting up a secure VPN infrastructure which combines IT and OT comes along with a high effort in handling and coordination, especially in case of IT-Security. This includes e. g. establishing a secure connection, updating of certificates, or generating data flows.
A secure and scaleable Connection is crucial for the realiszation of IoT projects.
Easy build up of secure industrial VPN infrastructures to connect devices and machines
With our software solution Welotec VPN Security Suite users benefit from a fully automated VPN infrastructure enabling connectivity and secure access to devices like HMI, PLC, IPC and machines in the field. It comes with an easy deployment, brings flexibility in case of applications and ads an additional security layer to the network infrastructure. The advantages at a glance:
- Easy setup of automated industrial VPN infrastructures
- Docker VPN: Supports devices with Container Runtime or OpenVPN
- VPN concentrator with integrated firewall
- Embedded PKI for automated certificate handling
- Device management for easy rollout of configurations and updates
- On-premise solution
- Own WebUI for central administration
- REST-API for integration into ERP, Monitoring or SIEM
Industrial VPN router for IPC remote access
Funktionality of Welotec VPN Security Suite
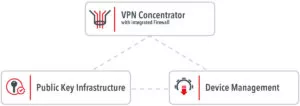
The Welotec VPN Security Suite offers automated processes to roll out and manage VPN infrastructures. It consists of three components. This includes a central VPN Concentrator with integrated Firewall and access rules. An integrated Public Key Infrastructure (PKI) manages and renews digital certificates. The third component is a Device Management for rollouts and distributing configurations.
Fig. Structure of Welotec VPN Security Suite
The VPN Concentrator bundles the incoming VPN connections, assigns fixed IP adresses and handles routing and NAT.
An integrated PKI automatically creates device-specific certificates. All client VPN certificates are signed by a central authority. In this way, trust is maintained from the end device to the central and parent Certificate Authority or CA for short. Instead of the integrated CA, a user‘s own CA can also be used. It is also possible to connect a user‘s own PKI.
The device management automatically distributes the certificates and VPN configurations. This works with Welotec devices or Docker Container enabled devices, which are connected via VPN Container Client (VPN-CC). Welotec devices additionally support template-based management of firmware and device configurations.
High device compatibility and application flexibility for secure industrial VPN tunnels
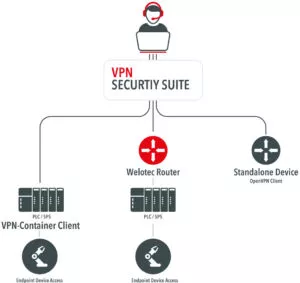
Depending on application and frame conditions, users face different challenges how to implement a secure VPN infrastructure. With Welotec VPN security suite users are equipped with a solution opening a wide range of possibilities for best IT and OT convergence, also in the case of hardware retrofitting. Below please find a short overview of the relevant connection possibilities:
- Connection to end devices via Welotec TK800 VPN Router. In case of mass deployment, the rollout can be managed via Zero-Touch-Provisioning (see use-case down below).
- Connection to end devices with Docker Container: integrated VPN Container Client for quick generation of of VPN infrastructures. Rollout can be deployed through Cloud, Docker Swarm or Kubernetes.
- Access to stand-alone devices via OpenVPN
- Industrial VPN Router for IPC remote access
Fig. Device compatability – Welotec VPN Security Suite
Implications for Business
The successful implementation of a VPN infrastructure not only has advantages in terms of the implementation process or IT security. It also provides users with access to important data, which nowadays is the most important resource for business success.
Data Generation
- Data gathering for increased efficiency and better decision making (e.g. maintenance or predictive maintenance)
- Improved analysis and processing through integration of data into third party systems via API (e.g. Big Data or Monitoring)
Remote Access
- OT VPN – Secure industrial remote access to distributed devices and connected machines from all around the world – 24/7 access
- Increased efficiency through less effort in travel and staff presence
Business Model
- Better service quality through predictive maintenance and reduced down-times
- Potential for new services and business models (e.g. Software-as-a-Service, Equipment-as-a-Service)
Use Case: building a VPN tunnel with Welotec VPN Security Suite and TK800 4G LTE VPN Router
Step 01
Welotec TK800 Router is pre-configured at Welotec Factory and SIM is installed.
Step 02
Devices (e.g. 10x TK800 Router) are shipped to the customer
Step 03
Customer install TK800 at the machine, connect 4G antenna, Ethernet Cable and Power.
Step 04
TK800 is going online and showing up in the Welotec VPN Security Suite (self-registration).
Step 05
Customer can activate TK800 in the Welotec VPN Security Suite and assign a configuration.
Step 06
Configuration and Credentials are installed in the TK800.
Step 07
Secure Remote Access from a Computer – over the Welotec VPN Security Suite – to the device behind the TK800 (e.g. a PLC) is seamless possible.