How to implement efficient intrusion detection on substation level
In modern substations there are countless digital devices and software systems that control the power supply (Fig. 1). This is especially true in substations that are fully automated according to the IEC 61850 standard. Not only do the devices actively interact with the remote control center. They also communicate with each other within the substation networks and respond automatically to new information from other systems – without interference from the control center.
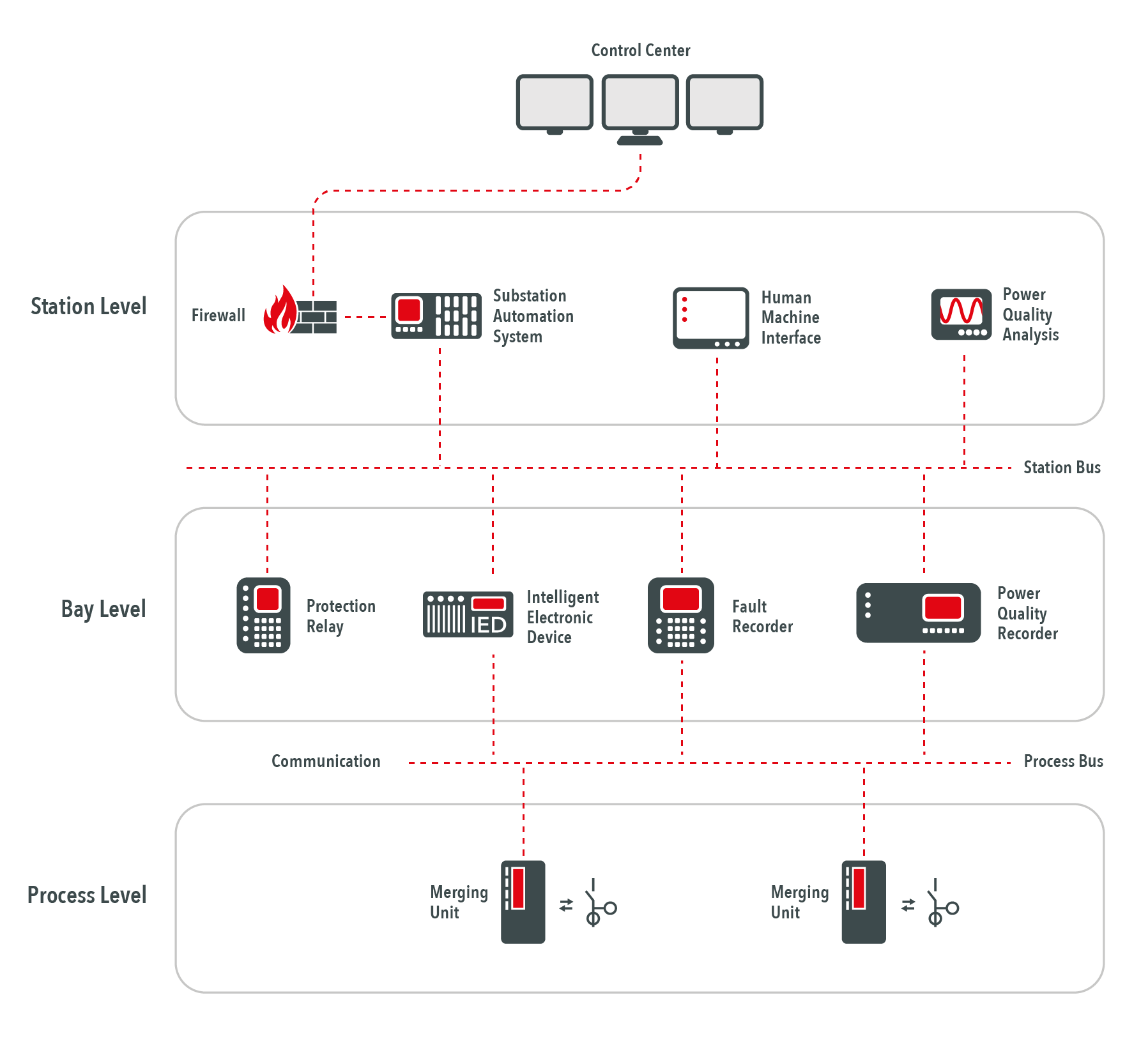
Consequently, it is important that the communication between the devices cannot be manipulated and lead to unwanted incidents such as blackouts.
In the past, firewalls were considered a sufficient tool to prevent third-party access to the devices and equipment running in the substation. They block the most common attack vectors. However, they are only as powerful as their signature-based blocklist is complete. Beyond that, they are blind. They do not detect novel attack patterns, nor do they detect attacks that occur through authorized access points. And they certainly do not detect problematic or malicious communications within a substation.
Cyberattacks on substations are no fiction
The years 2015 and 2016 have already shown that these risks are quite realistic, especially in times of crisis. On December 23, 2015, the Ukrainian capital Kiev experienced its first blackout due to targeted cyberattacks. The attack was carried out on several substations using BlackEnergy and KillDisk malware. The attackers took control of multiple workstations using compromised VPN access, disrupted the power supply and made remote recovery impossible.
The following year, the attackers again gained access to the corporate network of an energy supply company via spear phishing. From there, they moved laterally through the network for several months until they were able to transition to the Operational Technology (OT) of a 330 kV substation. This time, instead of remotely taking over the workstations, they used malware specifically tailored to the IEC 60870-5-104, IEC 60870-5-101 and IEC-61850 protocols. With these, they automatically shut down the substation on December 16, 2016, and blocked remote recovery.
Ensuring the visibility of the inside at all times
Because of the risk surface described above and the scope of the impact a cyberattack will cause on a substation, the defense-in-depth approach is recommended for electric utilities (utilities). This approach is based on three observations:
- Professional attackers are always at least one step ahead of traditional (signature-based) defense mechanisms.
- Sooner or later, professional attackers gain access to the network.
- There is no such thing as 100 percent perimeter security.
For OT networks, these real-world observations pose a particular risk. This is because OT devices and industrial protocols are still characterized by a lack of security mechanisms of their own. They are “insecure by design.” For example, the MMS, GOOSE and IEC-104 protocols classically used in substations can be exploited for man-in-the-middle attacks. In these attacks, the attackers (virtually) put themselves between two devices and impersonate each other. In the direction of the control center, attackers can thus pretend that everything is running according to plan in the substation, while malicious commands are given to the actuators (e.g., relays or breakers).

Of course, Defense-in-Depth does not mean that standard security mechanisms such as firewalls, VPN security and authentication become obsolete. However, they need an extension – a second “Line of Defense”. An automated and highly networked OT must be secured like a modern state or city-state (Fig. 2). The city wall and gatekeepers (firewalls, data diodes, authentication) secure the state externally against easily detectable enemies (signatures). The police, constitutional protection authorities and intelligence services (anomaly detection) are responsible for internal security in the state. They are responsible for detecting successful intruders at an early stage based on their activities, which usually differ from those of normal inhabitants. This internal security can be established by OT monitoring with anomaly detection.
How does anomaly detection work in a substation?
The sensors of this threat and intrusion detection system are easily integrated into the substation’s OT via network taps or switches. Within a few minutes, all communication within the substation can be monitored and assessed. Not only does this give utilities full visibility into their substations (Fig. 3). They can also detect any anomalies in their communications.
Anomalies include all communication processes that deviate from the expected, established communication. In IEC 61850 infrastructures, the Substation Configuration Description file (.scd) is used for baselining or training the anomaly detection. The anomaly detection then continuously checks the communication in the substation for changes. This also makes successful third-party access and man-in-the-middle attacks immediately visible. It does not matter whether this anomalous behavior comes from a “stranger” (an attacker) or a regular resident of the fortress (for example, an administrator). It’s enough that it’s different.

OT monitoring and anomaly detection with Welotec
Since 2021, Welotec provides these functions of an OT monitoring with anomaly detection on its IEC 61850 Substation Server.
The Welotec Substation Server (RSAPC) is a virtualization server for use in substations. The hardware is certified in accordance with IEC 61850-3 and IEE 1613, making it ideally suited for operation in electrical substations.
Most power supply companies are already using Welotec’s IEC 61850 Substation Servers (RSAPC). Applications such as HMI, substation gateways, engineering workstations and firewalls usually run on such a hypervisor.
Thus, energy companies do not need to install any additional hardware or software in their substations besides the Welotec Substation Server in order to establish OT security. Rhebo’s OT monitoring with anomaly detection can simply be started as another virtual machine.
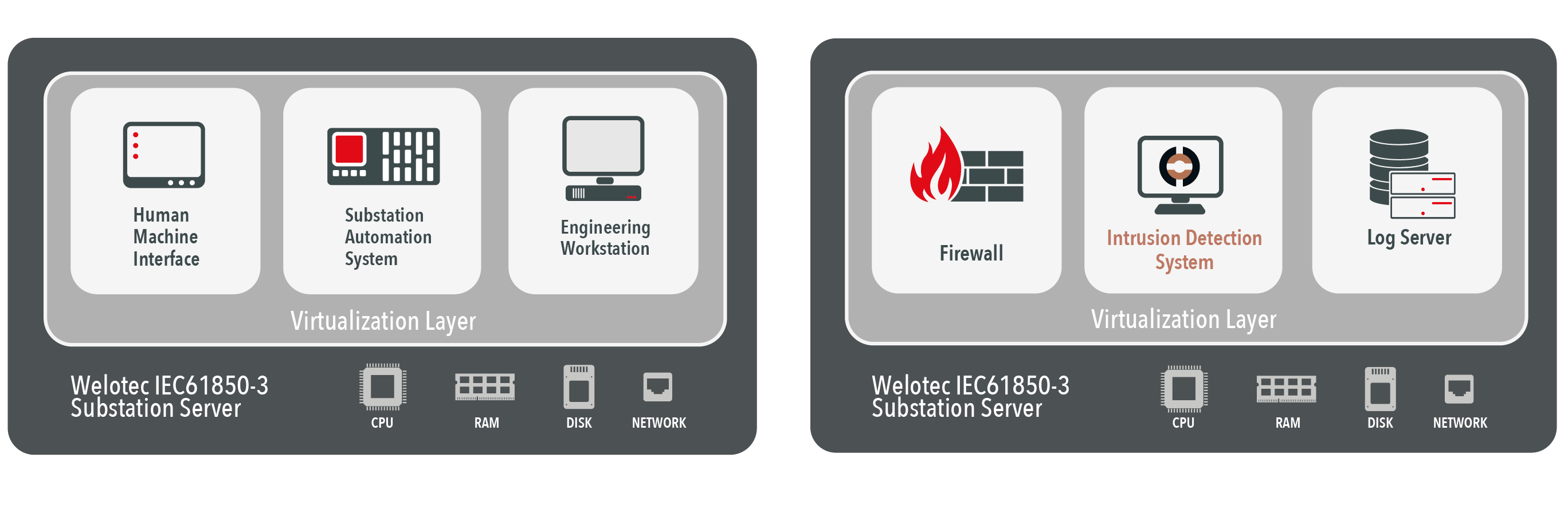
The platform character of the Welotec Server thus also allows efficient use of hardware in substations. In addition to OT monitoring, other functions such as firewall, log server, engineering workstation and the entire substation automation system can be integrated on the hardware platform (Fig. 4).
As a result, utilities can cost-effectively drive digitalization and automation in their substations without losing sight of cybersecurity.
For more information on the joint solution from Rhebo and Welotec:

